CEH Practice Test iOS
Unlock your path to becoming a Certified Ethical Hacker with CEH Practice Test!
Our app is meticulously engineered to propel your exam preparation, immersing you in a dynamic and authentic testing environment.
Dive into an exhaustive range of practice questions that encompass all critical domains essential for your CEH certification journey.
Each question is accompanied by an elaborate explanation, refining your insights and fortifying your cyber skill set.
Key Features:
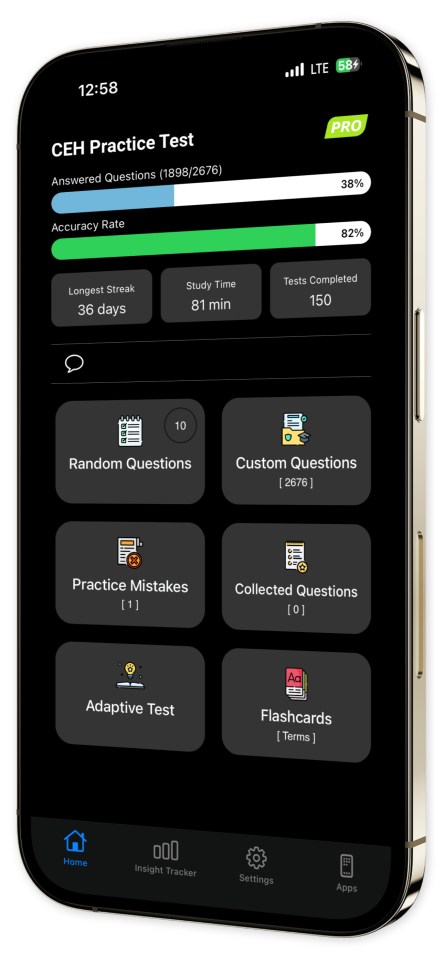
- Extensive Question Bank:
Delve into hundreds of meticulously crafted questions covering pivotal topics to ensure comprehensive exam readiness.
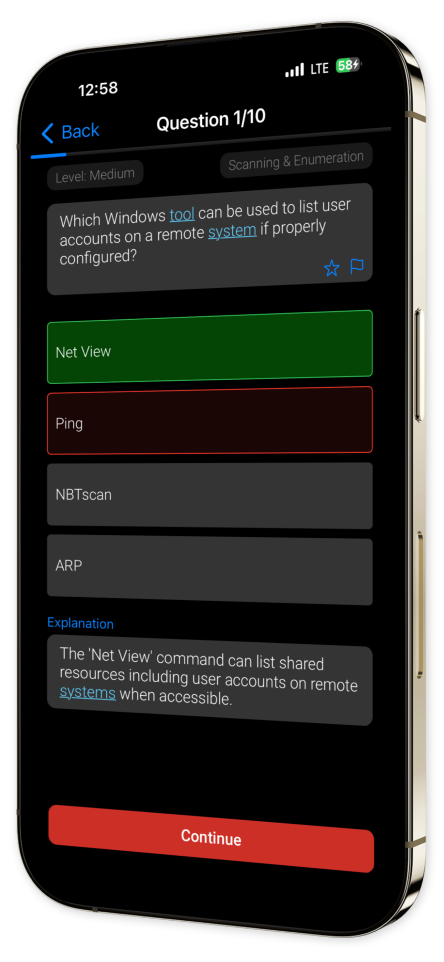
- In-Depth Explanations:
Enhance your understanding with each question through thorough explanations that elevate your learning curve.
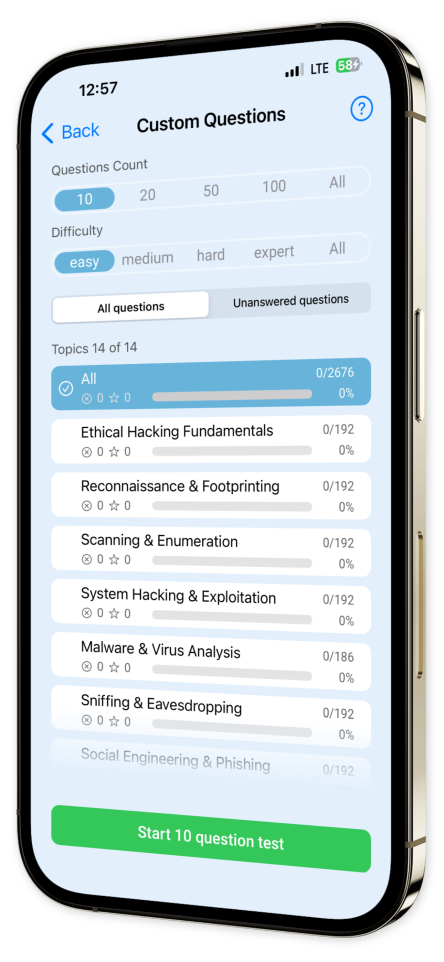
- Custom Test Creation:
Craft personalized quizzes by choosing specific topics and question styles, tailoring your studies to target your unique areas for improvement.
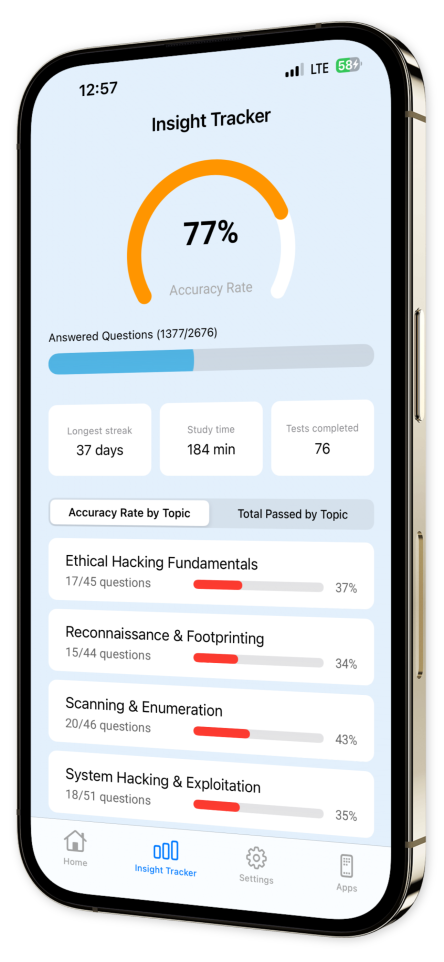
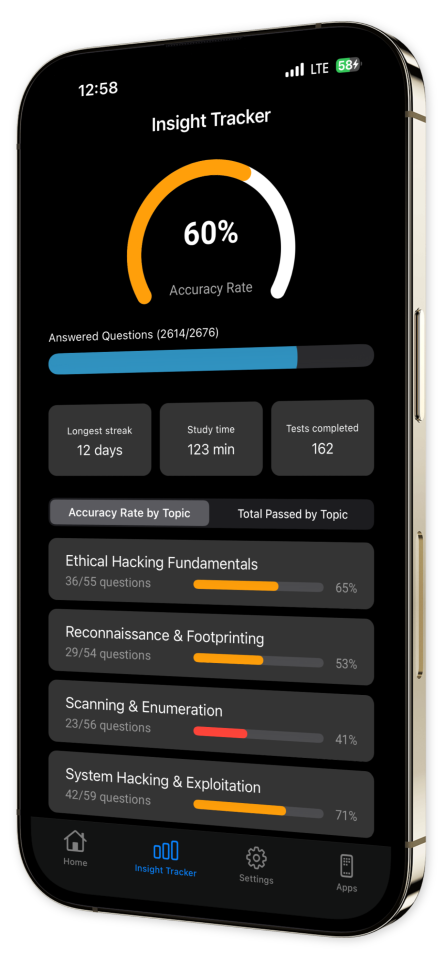
- Progress Tracking:
Monitor your advancement over time with our sophisticated progress tracking system, helping you recognize strengths and pinpoint weaknesses.
- Offline Access:
Enjoy the flexibility to study on your terms, anywhere and anytime, even without internet access, perfect for learning on-the-go.
- User-Friendly Interface:
Experience an optimized and intuitive design, ensuring seamless navigation and focus on mastering CEH content.
Embark on a robust preparation journey with CEH Practice Test. Your mastery of ethical hacking commences here.
Download CEH Practice Test today and fortify your exam preparation with a smart, efficient, and engaging approach.
Take control of your future in cybersecurity – conquer the CEH exam with confidence and precision!
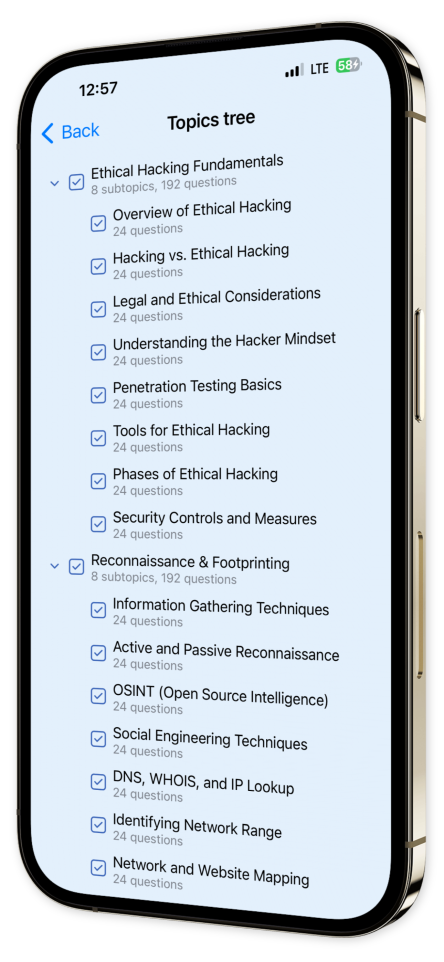
Content Overview
Explore a variety of topics covered in the app.
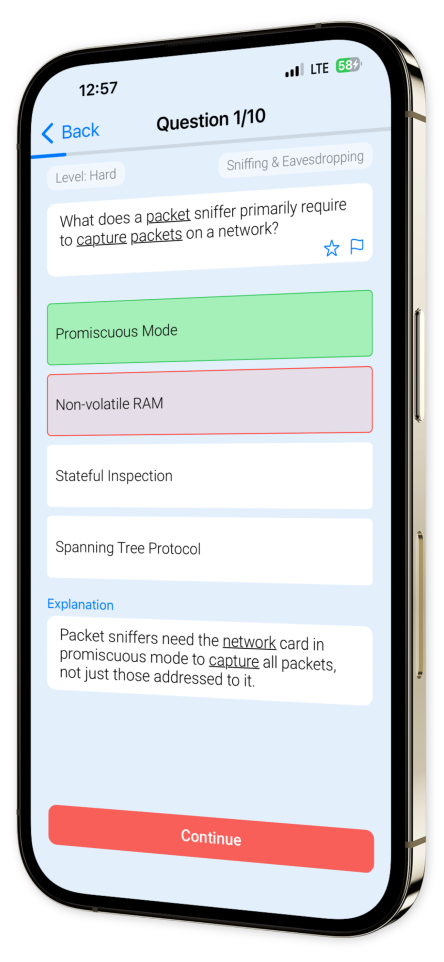
Example questions
Let's look at some sample questions
In ethical hacking, what does the term 'white hat' refer to?
Malicious hackerUnauthorized accessSecurity professionalPenetration test
A 'white hat' hacker is a security professional who uses hacking skills to find and fix security vulnerabilities ethically.
In an ethical hacking context, why is maintaining a strict scope important?
Ensures thorough attackSimplifies documentationPrevents unauthorized probingMaximizes test coverage
Maintaining a strict scope ensures ethical boundaries are respected and prevents unauthorized probing.
What is the primary ethical concern when conducting penetration tests?
Avoiding system downtimeGaining unauthorized accessObtaining explicit consentMaximizing data exposure
Without explicit consent, penetration testing violates ethical and legal standards, risking unauthorized access and privacy violations.
Who usually performs ethical hacking?
Random individualsMalicious usersCertified professionalsCompetitors
Ethical hacking is performed by certified professionals for securing systems, under legal arrangement.
A company wants to test its security. Who should perform the assessment to ensure ethical standards?
Black hat hackerGray hat hackerWhite hat hackerScript kiddie
White hat hackers conduct security assessments legally and ethically, following agreed guidelines.
Which scenario exemplifies ethical hacking over hacking: accessing a system without detection or conducting a penetration test for security enhancement?
Accessing a system silentlyBypassing authentication undetectedExecuting a penetration test with consentPlanting malware to test network response
Ethical hacking conducts penetration testing with consent to find vulnerabilities, unlike hacking that aims to bypass defenses without detection.
What is the test for liability under the CFAA for exceeding authorized access?
Breach of fiduciary dutyIntended gain is achievedAccessing for fraudulent purposesCausing loss of $5,000 or more
Under the CFAA, liability for exceeding authorized access often hinges on causing a loss of $5,000 or more or other specified outcomes.
A hacker uses a computer in Germany to attack a U.S. server. Which jurisdiction applies?
Only German lawU.S. and German lawOnly U.S. lawNone apply if anonymous
Cybercrime often involves multiple jurisdictions. Both U.S. and German laws could be applicable depending on specific treaties and agreements.
What impacts legal liability in ethical hacking?
Ethical intent onlyScope boundariesHacker's experienceAudit trails only
Adhering to defined scope boundaries in a hacking engagement is crucial to avoid legal liability and ensure assent is followed.
Ethical hackers use the mindset of a hacker primarily to:
Design video gamesWrite malwareEnhance software usabilityIdentify system vulnerabilities
Ethical hackers use their mindset to identify system vulnerabilities to prevent malicious attacks.